Cryptography is the conversion of plain ordinary text into unintelligible encrypted, hence secure data and vice versa.
If you can imagine a method by which the data you possess can be encrypted or made secure in such a manner that only the intended recipient can access, decipher and use it, then you have got the hang of it. Just remember the Alistair Maclean novels or WWII movies, where decoded messages were sent or received.
IOT this earlier method has been tremendously modified and modernized with the advent of computers. As most (if not all) of the data is nowadays sent through the internet. Using Cryptography, you can not only protect your information from being stolen or altered but also use it for authenticating the recipients too.
Table of Contents
Cryptography meaning
In earlier times, the meaning of cryptography was encryption only and nothing more than that. Nowadays, with the advent and practice of higher mathematical theories and data science techniques, it has evolved hugely. Modern Cryptography is concerned with mainly the following salients:
- Authentication: This plainly means that the sender and the recipient can confirm each other
- Integrity: Data sent cannot be altered, hence it remains safe and totally secure
- Confidentiality: Even if your information becomes public, no one would understand what it meant
- Non-repudiation: Any sender, once the data is wired, cannot deny their motive in the transmission
Cryptography origin
Before digging deep into how we use cryptography today, know how it started:
Ancient World
Astonishingly, the tomb of Khnumhotep II, an Egyptian nobleman, which dates back to 1900 BC, contained the first trace of Cryptography. Pieces of evidence have unearthed facts that the ancient Egyptians, Assyrians, Greeks, Hebrews, and Babylonians all used Cryptography.
Spartans, for example, used a cipher device “The Scytale“. This was primarily to be used by military commanders in the battle for secret communications. Hence, Greeks were the pioneers and most probably, the inventors of the Transposition Cipher in its ancient form. Aeneas Tacticus in his book, “On the Defense of Fortifications” dating to the 4th Century BC, devoted a whole chapter to Cryptography and its uses.
Polybius [c. 200 – 118 BC] made the Polybius Checkerboard, which arranged letters into symbolic pairs and hence encoded them for security. The Romans like Julius Caesar, and later Augustus Caesar, all used various forms of Cryptography for their confidential letters. In Stanley Kubrick’s 1968 masterpiece “2001: A Space Odyssey“, the computer HAL encrypted to IBM using the cipher code of Augustus Caesar.

Medieval times
Arabs understood the uses of Cryptography and devised both transposition and substitution ciphers extensively. Al-Kalka-Shandi, in his 1412 encyclopedia “Ṣubīal-aīshī“, included several Cryptographic techniques and even furnished explicit instructions on encryption in detailed forms.
Gabriele de Lavinde, serving Pope Clement VII in 1379 AD, wrote a manual on Cryptography, which was perhaps the first in Europe. The first Cipher in disk form was described by Leon Battista Alberti in his famous “Trattati in cifra“ (or the Treatise on Ciphers). This device was exactly replicated and used extensively by the Signal Corps of the United States Army in World War I for tactical communications.
Giambattista Della Porta in his 1563 treatise entitled “De furtivis literarum notis” (or the The Notorious Secret Literature) furnished the earliest known example of a digraphic cipher. Blaise de Vigenère published in 1586 his “Traicté des chiffres“ (or the Treatise on Ciphers) containing the elaborate descriptions of the square table which now bears his name. This remains the first example of an Encryption/Decryption table.
Modern Era
During the American Civil War in the early 19th century, all diplomatic communications started to be sent using codes only. The Confederate Army used the Vigenère cipher primarily in their communication and sometimes, monoalphabetic substitutions. However, these were mostly deciphered by the Unionists.
On the contrary, Confederates were not so lucky; sometimes they even resorted to appealing to the readers of the Newspapers in the Southern states, asking for help in decoding the Union ciphers they could obtain.
The general public in this era of sharing knowledge and applying thoughts to starting inventions provided some dramatic examples of coding and decoding on their own. A famous example is the 1820’s the Beale Cipher, reputedly supposed to provide the hidden location of buried treasure in Bedford County, Virginia.
The American Edward H. Hebern in 1917 made the first patent claim with respect to Cryptography, by being the first to realize the complex substitutions that could be achieved by connecting rotors properly in place of monoalphabetic substitutions that were earlier used.
World War
Rudimentary but better versions of Cryptography and its many techniques of this era spilled over to the 20th Century; eventually the First World War. During this war, most countries devised and used several codes and employed mathematicians and statisticians to both encrypt their own channels of communication. They would also know how to decrypt the enemy’s messages. Thus, the Cipher systems began to be used more and more extensively as the years went by. The ADFGVX fractionation cipher, developed by the Germans remains the most famous of all Ciphers at this juncture.
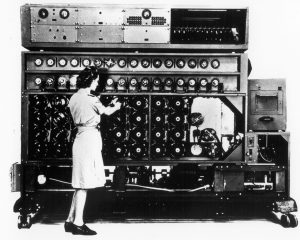
During World War II, the Nazis designed the Enigma Code that was used to encode strategic communication. It was first deciphered by the Polish rebels under Marian Rejewski in the early 1930s, and then properly by Alan Turing of England later.
Types of Cryptography
Nowadays, Cryptography primarily has three types of modern techniques. They are:
Hash Functions
In this algorithm, you don’t need to use any key. That is why a lot of Operating Systems [yes like Microsoft Windows for example] use Hash Functions for the purpose of encrypting passwords. It involves the precise computation of a definite length hash value, depending upon the original and unimposing plain text. Once done, it makes it almost impossible for anyone except the intended recipient to decipher the contents.
Public-Key Cryptography
In this type of Cryptography, not one but two types of standard keys are used always. Yes, you guessed it; one for the masses i.e. the Public Key which may be freely and openly distributed, while the other paired one – the Private Key remains hidden to the public eye.
The first type of key here is used for the general encryption of the data, and the latter is used for the decryption of the encrypted data. In the last 300 – 400 years of algorithm technology, this is perhaps one of the most, if not the premier revolutionary concept. Last but not the least, it is also commonly known as Asymmetric-Key Cryptography.
Symmetric-Key Cryptography
Compared to the earlier method, this may seem much simpler. Here, both the sender and the recipient share a single key. Means if you are the sender, the key you possess is also got by the person you want to send the data to. Basically first you encrypt the data from the plain text, and send the cipher text to whosoever you desire, along with your key of course. This recipient of your choosing then uses that same key to decipher said data.

Examples of Asymmetric and Symmetric Cryptographic
Asymmetric or Public-Key Cryptography is required for Digital Signatures for providing online security and thus also for User Authentications, and even for key exchanges. Common applications include
- RSA [named after its three famous inventors: Rivest, Shamir and Adleman] – This is the most common technique used in electronic commerce, Digital Signatures etc
- PGP [Pretty Good Privacy] aids in proper Authentication in basic communication of important data, and also protecting confidential emails
- SSL [Secure Socket Layers] and TLS [Transport Layer Standard]: These are commonly used all over the Internet nowadays for securing data in websites, commonly hosted platforms and basic streaming of information everywhere
- GNU Privacy Guard is used to track OpenPGP [Open Pretty Good Privacy] specifications only
Symmetric Cryptography or as you should call it, symmetric encryption is Cryptography at its fastest! This is simply because the keys used here are shorter, faster and hence can be used more efficiently. Thus, for any given set of resources that need to be computed, this type of encryption can handle more volumes of data. And this is actually true for any given time. It is being used in the following areas
- Two Fish
- Misty 1
- AES [Advanced Encryption Standard]
- Camelia
- IDEA [International Data Encryption Method]
- Skipjack, and
- DES [Data Encryption Standard]
Cryptography and Network Security
What is Cryptography as far as Network Security is concerned? You guessed it: everything! Nowadays, cybersecurity is becoming more and more important to safeguard all private information and transactions, and here Cryptography is playing an ever-increasing role. It aids in securing data and its safe and seamless transmission.
Cryptography protects sensitive and confidential information from being distributed, hacked into, from virus attacks online, online eavesdropping et al. Otherwise, there would have been complete chaos over every important information and private data being openly circulated over the web and being completely unsafe.
Cryptography Algorithms
Cryptographic Algorithms or Ciphers, as they are more commonly known are the common means by which you can actually alter data from normal [called plaintext] i.e. their usual form to a more secure and encrypted [called ciphertext] form: and then again back to their readable format.
Encryption: method of changing plaintext to ciphertext
Decryption: method of changing ciphertext to plaintext
Most commonly trusted Algorithm
AES [Advanced Encryption Standard] is arguably the most common and the most widely trusted algorithm in the whole cyber world and is to be found being used for most day-to-day digital work across the globe! It is pretty efficient in its standard form which is 128-bit. But for circumstances which warrant stronger measures and tougher encryption purposes, it also can use 192-bit and also 256-bit. AES is the standard of the US Government: also used by several countries and a number of international companies!
Some other forms of common Algorithms are
- Hashing Algorithms – You can use these algorithms for providing data integrity
- Signature Algorithms – These, as the very name suggests, are the ones used globally for putting Digital Signatures to data, which can then be authenticated for the mutual protection of the sender and the recipient
- Encryption Algorithms – You can use these to encrypt any given data basically! They provide confidentiality
What is Cryptography used for
As you may have understood by now, Cryptography has a wide range of usage in our daily work. Its use is growing exponentially by the year, as more and more work is now being digitized. As a result, securing said information is becoming the need of the hour, and what is Cryptography but the means to provide the same!
The general applications are Digital currencies, Military Communications, Chip-based payment cards [like your AMEX, VISA, MasterCard et al] and thus most types of e-Commerce. Companies like Amazon, for instance, depend hugely on the general Cryptographic techniques. The process makes buying and selling safe, not only for them but also for millions of users across the world.
Last but not the least, even the common passwords that you may put, like the one for your Personal Computer at the leisure of your home, or the Work Station at your office, or for that matter even those for your Facebook, Twitter & Gmail accounts, all use the standard encryption methods to safeguard your private information and files!
In everyday life, Cryptography can be found in the following:
- Electronic Money
- Digital Signatures
- Disk Encryptions
- Secure Network Communications
- Time Sampling
- Anonymous Remailers
Cryptography in Movies
An easy way to understand what is cryptography is by watching blockbuster movies that exhibits its usage. These range from “ A Christmas Story “ [1983] to “ The Imitation Game ” [2014] and the latter was about Alan Turing, the real-life hero who helped the then British Intelligence crack the Enigma code. This was the most advanced encryption method being used by the Nazis to mask their communications! Other notable mentions can be “ Sneakers “ [1992], “ The Da Vinci Code “ [2006], “ Girl with the Dragon Tattoo “ [2011] and “ Skyfall “ [2012].